1.1.a – Access Ports (Data and Voice)
Access ports are used to transmit traffic on a single VLAN that it has been assigned. (There are also Trunk ports which can carry traffic for all VLANs accessible to a switch)
There are two VLAN ranges you can use:
Normal Range 1 – 1001 (VLAN 1002-1005 are reserved for Token Ring and FDI.)
Extended Range 1006 – 4094
There are some differences between the two, both are covered below and will be covered further in later sections.
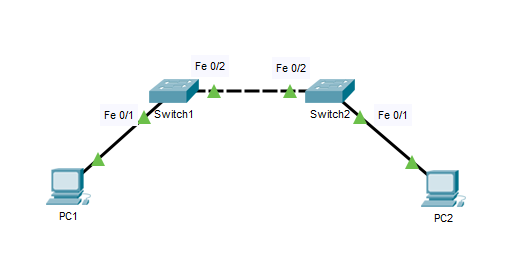
We’re going to look start by looking at a simple VLAN setup. With two end devices connected via 2 switches.
Replicate the setup below on both Switches:
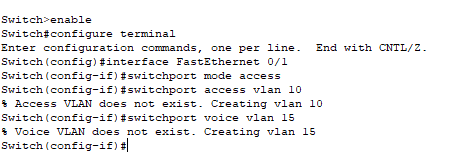
configure terminal
interface FastEthernet0/1
switchport mode access
switchport access vlan 10
switchport voice vlan 15
Then on the switches configue a trunk on the port that connects them together:
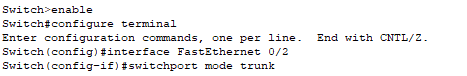
configure terminal
interface FastEthernet0/2
switchport mode trunk
And that’s all there is to it , you now have 2 devices that can communicate over that VLAN.
If you want to do this with a VLAN outside the range of 1-1005 you need to run another command on both of the switches.
If for example you want to use VLAN 3000, you’ll also need to configure the ‘allowed vlan list’ on the Trunk to let the traffic flow.
So on the interface that has the trunk set up issue this command:
Switch(config-if)#switchport trunk allowed vlan add 3000
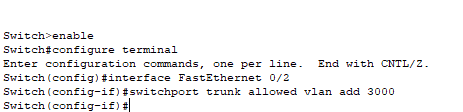
switchport trunk allowed vlan add 3000
1.1.b – Default VLAN
This is the VLAN to which all access ports are assigned to until they are explicitly places in another VLAN. On Cisco switches this is VLAN 1
Leaving ports on the default VLAN can be a security risk. Ideally you’ll put all unused access ports on a different VLAN, and not use VLAN 1 for traffic.
This is different from the native VLAN, the native VLAN can be changed and represents the VLAN that all untagged traffic gets put on automatically.
NOTE – When dealing with Trunks the most useful command for debugging is show interfaces trunk – just a tonne of useful readable data.